-
How do cyberattackers breach your security perimeter?
Cyberattackers look for loopholes or vulnerabilities in your IT framework that are often easy to miss. These loopholes can be found just about anywhere: a weak password in your company laptop or a malware attachment in a phishing email, for instance.
-
5 ways to strengthen your security posture
Strengthening your security posture begins by choosing security practices that make you less prone to loopholes and more resilient to attacks. Here are five ways you can tip the scales in your favour.
-
Improve your security posture with CDW’s cybersecurity experts
At CDW, we can help you prepare, defend and respond to cybersecurity threats. Our expert cybersecurity teams offer advice and solutions that are tailored to your unique organizational framework and deployment strategies.
April 18, 2024
5 Strategies to Help Improve Your Security Posture
As cyberattacks become more prevalent, your organization must ready itself with the right practices and technology. Here are five simple yet impactful ways organizations can build cyber resilience, enabled by our cybersecurity partners.

“What could have we done to prevent this?” is a common question asked once an organization has suffered a cyberattack. A thorough investigation is sanctioned, affected resources are repaired and at times, customers are reimbursed.
Fortunately, organizations with a strong security posture are less likely to be asking this question because they have implemented security measures to reduce the chances of a successful cyberattack.
As cyberattacks become more prevalent, your organization must ready itself with the right practices and technology. In this blog, we uncover five simple yet impactful ways organizations can build cyber resilience as suggested by our experts and enabled by our cybersecurity partners.
How can cyberattackers breach your security perimeter?
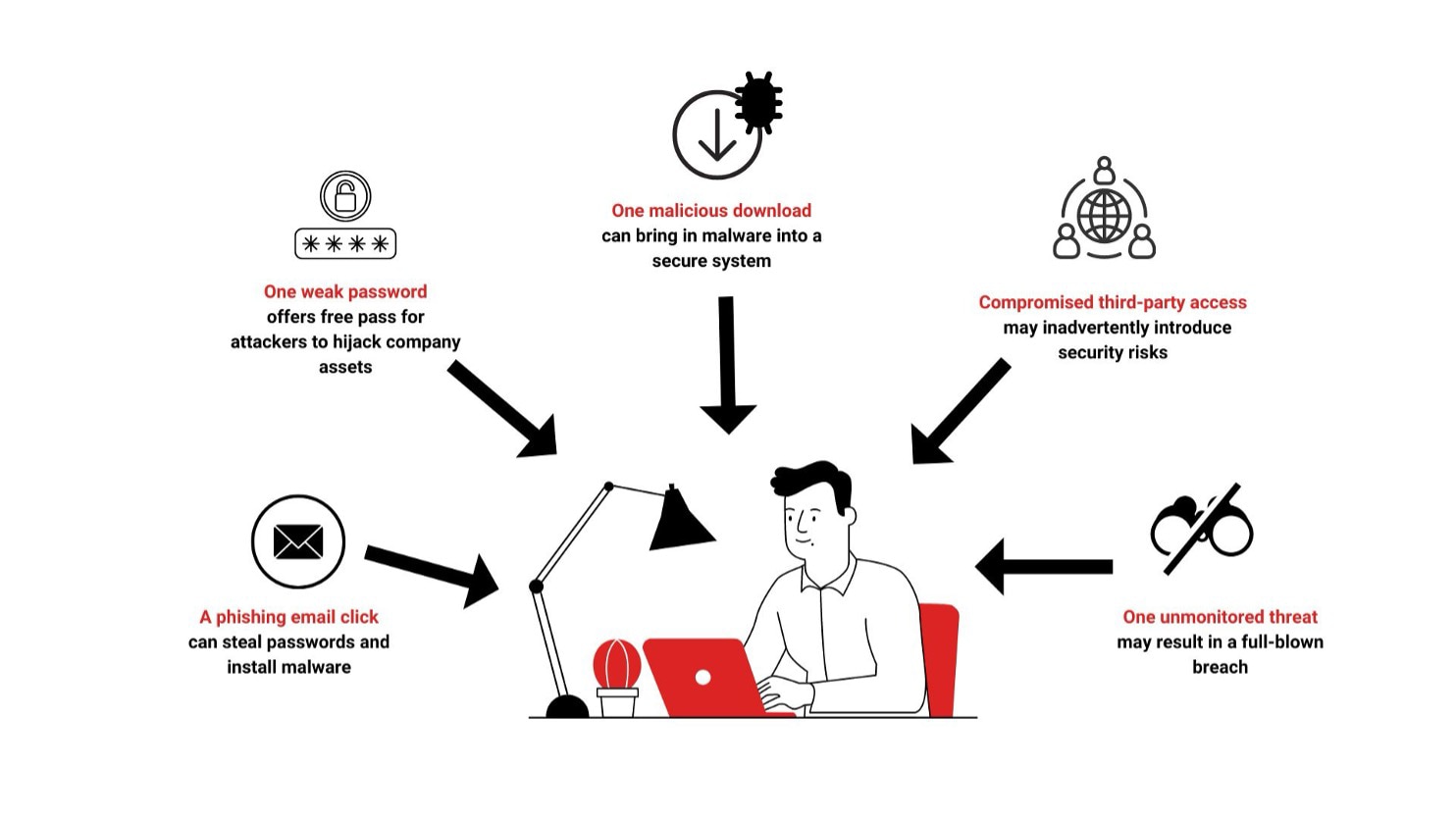
Cyberattackers look for loopholes or vulnerabilities in your IT framework that are often easy to miss. These loopholes can be found just about anywhere: a weak password in your company laptop or a malware attachment in a phishing email, for instance. As your organization grows bigger and more complex, catching and fixing them becomes harder.
Sometimes, a loophole that can let attackers in may not look suspicious at all. Let’s consider this series of events.
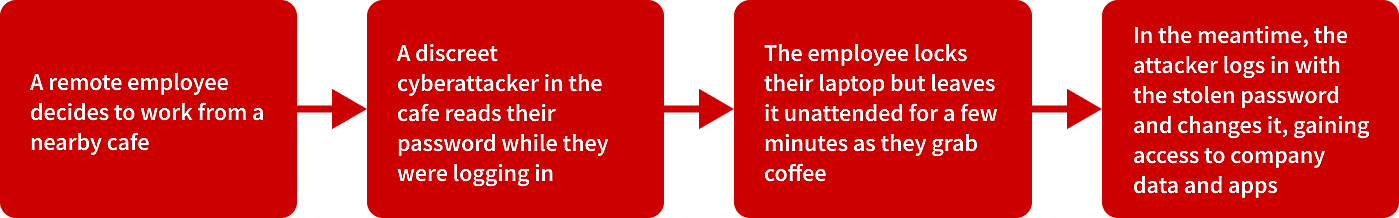
Here, the loophole that let the attacker in was a combination of a weak password and lack of multifactor authentication which would have otherwise alerted the employee.
While working from a cafe is completely acceptable, organizations need to ensure they have the proper security measures in place for their employees. As thousands of employees choose remote work, organizations expand their digital front and cloud computing becomes the norm, each organization will have more potential loopholes to cover.
Lately, cyberattackers have grown extremely sophisticated in finding loopholes. For instance, CDW’s Canadian Cybersecurity Study revealed that 9-10 percent of all cyberattacks turned into cyberincidents.
Their common targets span not just employee laptops but the entire breadth of IT assets, including the following:
- SaaS applications
- API endpoints
- Database appliances
- Network appliance endpoints
- Virtual servers
- IoT devices
- Client computing devices
The bottom line is that the next attack could come from anywhere. Canadian organizations, whether private companies or public sector institutions, need to ensure they have a strong security posture to defend against attacks.
5 ways to strengthen your security posture
Strengthening your security posture begins by choosing security practices that make you less prone to loopholes and more resilient to attacks.
This process would look different for each organization based on their individual needs and goals. Yet, there are common best practices that will benefit most organizations to help stay one step ahead of the attackers.
Here are five ways you can tip the scales in your favour.
1. Secure your endpoints
Everything from laptops, printers and network routers to IoT devices are considered as endpoints, and as organizations grow and more workers are working remotely, these endpoints can become more difficult to track and manage.
Since these devices could all offer access to your network, attackers can use them as an entry point to steal valuable data. For instance, a vulnerable router may act as a point of entry to the entire company’s network filesystem.
Securing your endpoints blocks off attackers from entering your organization at the device level. CDW partners with a variety of cybersecurity vendors who offer the tools to help prevent an attack.
Absolute Secure Endpoint, part of Absolute’s security portfolio, can help organizations bake security into each endpoint with greater visibility and control. The provider offers endpoint visibility technology that is closely tied to the endpoint firmware. This helps IT teams keep track of the web of endpoints, even if they are powered off or are tampered with.
This approach enables IT and security teams to monitor endpoints, address security gaps and enable self-healing of critical applications, all of which are essential for maintaining a strong security posture.
How Absolute can help
- Always-on endpoint connection enabled by Absolute Persistence technology
- Self-healing capabilities that help IT teams better manage device lifecycle
- Improve device and inventory awareness for security compliance
2. Implement multifactor authentication
Multifactor authentication is based on two or more factors, including something you know (password or PIN), something you have (a physical key or device) or something you are (facial recognition). This can often take the form of a user being asked to enter an access code on their phone after typing their original password into their computer.
This additional step can help prevent an attack if an attacker steals an employee’s login credentials. Having your employees sign in through multifactor authentication can significantly reduce the chances of identity impersonation. However, if an attacker can trick the employee into entering the code on their phone, they may be able to successfully complete the MFA process themself.
Our partners at Yubico have come up with solutions to tackle this problem. Their MFA solution features a physical hardware security key called the YubiKey that supports a wide range of authentication protocols, making it a versatile tool in enhancing security and keeping your organization safe on the internet.
Yubico enables passwordless phishing-resistant MFA, which prevents SMS, authenticator or email bypass attempts. Their FIDO authentication standard uses cryptography to prevent it from being used by unauthorized cyberattackers. YubiKeys store no data and require no network connection, battery or client software.
How Yubico can help improve your security posture
- Step up authentication security with stronger, future-proofed, phishing-resistant MFA
- Useful for all organizations with stricter compliance needs, a remote workforce and shared workstations
- Simple deployment model for enterprises who need a large number of physical keys
3. Tighten password security with privileged access management
A shared password can create security vulnerabilities, especially if it falls into the wrong hands. If a coworker is unable to access a certain restricted resource, they should request for access through their own account rather than using someone else’s password temporarily.
This is the idea behind privileged access management (PAM) – attaching the right level of security clearance to login credentials.
Too many times, passwords are shared innocuously in the workplace but end up creating problems for IT administrators. PAM offers a framework for addressing this issue.
Our partners at Delinea have devised an intuitive and scalable method for implementing PAM across the diversity of access levels within an organization.
The Delinea portfolio is based on the Delinea Platform, which fundamentally has a set of shared capabilities from continuous discovery to audit analytics, MFA enforcement and the ecosystem of integrations.
At the top layer, their main solutions secure credentials, provide zero trust secure access and elevate privileges and entitlements. These primary use cases help customers to add layers of security to privileged activity. Identity threat detection and response allows customers to detect whether identities are overprivileged or accounts are misconfigured and remediate these issues to reduce risk quickly.
How Delinea can help improve your security posture
- End-to-end visibility – Gain new visibility into users and machine permissions, configurations and relationships
- Dynamic privilege – Manage all privileged authorizations across on-premises, multicloud and endpoints in one consolidated platform
- Adaptive security – Can support all types of environments and wide vendor integration
With the Delinea Platform, gain new visibility into user and machine permissions, configurations and relationships by extending the vault across all users. From human and machine vaults, manage all privileged authorizations – both standing and just-in-time (JIT) – across on-premises, multicloud and endpoints within a single consolidated platform.
The Delinea Platform offers wide vendor integration and delivers an engine that builds context around identities and assets. It provides insights into the attack surface to support the principle of least privilege and automatically adjusts the security posture. The architecture is future-proofed, designed for both legacy and cloud environments and can be deployed at the edge.
4. Catch and fix threats in real time
Our Canadian Cybersecurity Study found that the average downtime for various types of cyberattacks ranges from 12 to 18 days. Slow threat detection and remediation could be one of the reasons for this lengthy recovery.
There is an urgent need for modern threat detection and response tools that can root out the attackers sooner. Such tools can actively monitor threats across the organization’s cyberspace and help you take remedial action before it’s too late.
NETSCOUT’s Omnis Cyber Intelligence (OCI) offering can help organizations find potential threats without having to wait for days. Its real-time visibility features use machine learning to analyze network traffic and identify threats quickly.
OCI integrates global threat intelligence feeds to provide context and anticipate emerging threats. It’s flexible to adapt to various network environments, ensuring efficiency regardless of the organization’s size or complexity. The tool streamlines workflows and fosters teamwork among security analysts, enhancing threat response.
OCI provides complete visibility into your network, including data centres, colocation centres, cloud and remote workers. With complete visibility, adversaries are detected at every stage of their attack, including their actions after a computer is breached. The attacker may discover your network, move laterally and collect data. Without visibility into these actions, attacks can continue for months without detection. With complete visibility, you can change the outcome through early detection and remediation using NETSCOUT OCI.
How NETSCOUT can help strengthen your security posture
- Advanced network packet inspection capabilities offer nuanced threat hunting
- The solution extends to corporate data centres, user devices and cloud infrastructure
- OCI’s scalability ensures that it can cover the expanding attack surface for organizations on their digital growth journeys
ESET, a managed detection and response (MDR) provider, offers the same capabilities in a managed service offering. The company collaborates with IT teams within organizations to empower their threat hunting and response effectiveness.
The managed offering is useful for scenarios where organizations require cybersecurity expertise without wanting to hire in-house talent. It offloads the risks of detecting real-time threats while building robust security for the organization.
How ESET can help improve your security posture
- The company leverages a combination of ESET Inspect threat inspection capabilities and in-house security specialists to review potential threats
- Customers receive reports and actionable insights for improving their security posture
- Reduce the complexity involved in security upgrades with managed installation, support and deployment
5. Make sure your network trusts no one
Consider your network infrastructure as the bridge that connects your organization to the outside world. It allows you to serve your customers and work with vendors, but if it’s unguarded, it may let in cyberattackers.
This is why networks often become conduits for malware and entry points for exploits. To bolster network security, the zero-trust security model has become a preferred industry choice.
It places emphasis on configuring strict access controls and constantly validating all access requests, whether from inside or outside of the organization. The focus is on secure authentication and preventing unauthorized access.
The RUCKUS WAN Gateway (RWG) can be instrumental in enhancing network security for your organization when implementing a zero-trust network architecture. RWG ensures ongoing authentication and monitoring, aligning with the zero-trust principle of never trust, always verify.
It integrates with policy engines to grant users access only to necessary resources, minimizing unauthorized access risks. This solution can automatically trigger reauthentication in case of a breach, maintaining security integrity and keeping cyberattackers at bay.
How RUCKUS can help improve your security posture
- Supports IPsec and OpenVPN protocols, providing encrypted and secure data transfer across networks
- Adheres to industry standards and guidelines, offering a robust solution for secure network access and data protection
- Provides security for the five pillars of organizational security: identity, data, device, network and workload
Improve your security posture with CDW’s cybersecurity experts
At CDW, we can help you prepare, defend and respond to cybersecurity threats. Our expert cybersecurity teams offer advice and solutions that are tailored to your unique organizational framework and deployment strategies.
Our security operations centre (SOC) operates 24/7/365 with Canada-based experts trained in handling security events. Our services are backed by world-class security experts with numerous industry and partner certifications, including SOC 1, SOC 2, PCI, ISO 27001 and NIST CSF.
With the continuous support from our ecosystem of innovative partners, we bring the right advice for transforming security processes alongside the correct tools to help improve your security posture.
