-
Anatomy of a cyberattack
How would an attacker penetrate the system? Here are the five key attack components.
-
Build a stronger cybersecurity posture with Microsoft 365 Defender
Microsoft 365 Defender provides a comprehensive defence against sophisticated attacks across endpoints, email, identities and cloud apps. It automatically detects, investigates and remediates threats, reducing the workload for your security teams.
-
Step-by-step threat investigation with Microsoft 365 Defender
Microsoft 365 Defender offers four modules that seamlessly work together to build attack stories. Each module looks at the attack from an investigative angle, such as where did the incident start, which device was affected and so on.
-
Defend confidently with CDW’s cybersecurity expertise
Our security analysts monitor, analyze and resolve incidents around the clock, leveraging Defender for Endpoint’s robust capabilities and reducing the time and cost of dealing with cyberattacks.
February 29, 2024
How to Leverage Microsoft 365 Defender for Maximizing Cybersecurity in 2024
In this blog, David Izzard, Senior Manager of Executive Tech Strategy at CDW Canada, shares how organizations can investigate threats with Microsoft 365 Defender before they become security incidents.

Data breaches or cyberattacks designed to steal sensitive business data are not only trending upwards but are also getting incredibly sophisticated. According to CDW Canada’s 2023 Canadian Cybersecurity Study, 1 in 10 cyberattacks on Canadian businesses were successful in the past 12 months.
Such attacks can be very damaging as they might lead to heavy financial losses, eroded customer trust and sometimes may even result in regulatory fines.
Thankfully, for Microsoft customers, there are built-in defences against cyberattacks. Microsoft 365 Defender (or Microsoft Defender) offers a host of threat intelligence and remediation tools for Microsoft 365 users, which can detect and prevent cyberattacks with great efficacy.
In this blog, David Izzard, Senior Manager of Executive Tech Strategy at CDW Canada, shares how organizations can investigate threats with Microsoft 365 Defender before they become security incidents.
Anatomy of a cyberattack
“When it comes to cyberattacks, it's always all about the data,” said Izzard in a CDW webinar. The data contained in an organization’s IT infrastructure, a Microsoft 365 tenant in this case, could prove to be a goldmine for an attacker.
According to Izzard, most cyberattacks target three aspects of data:
- Confidentiality – stealing or extorting sensitive data
- Availability – blocking off access to critical data assets
- Integrity – tampering or manipulating the data
Whether the data would be stolen, tampered with or locked away depends on how the security controls are configured. But how would an attacker penetrate the system? Here are the five key attack components.
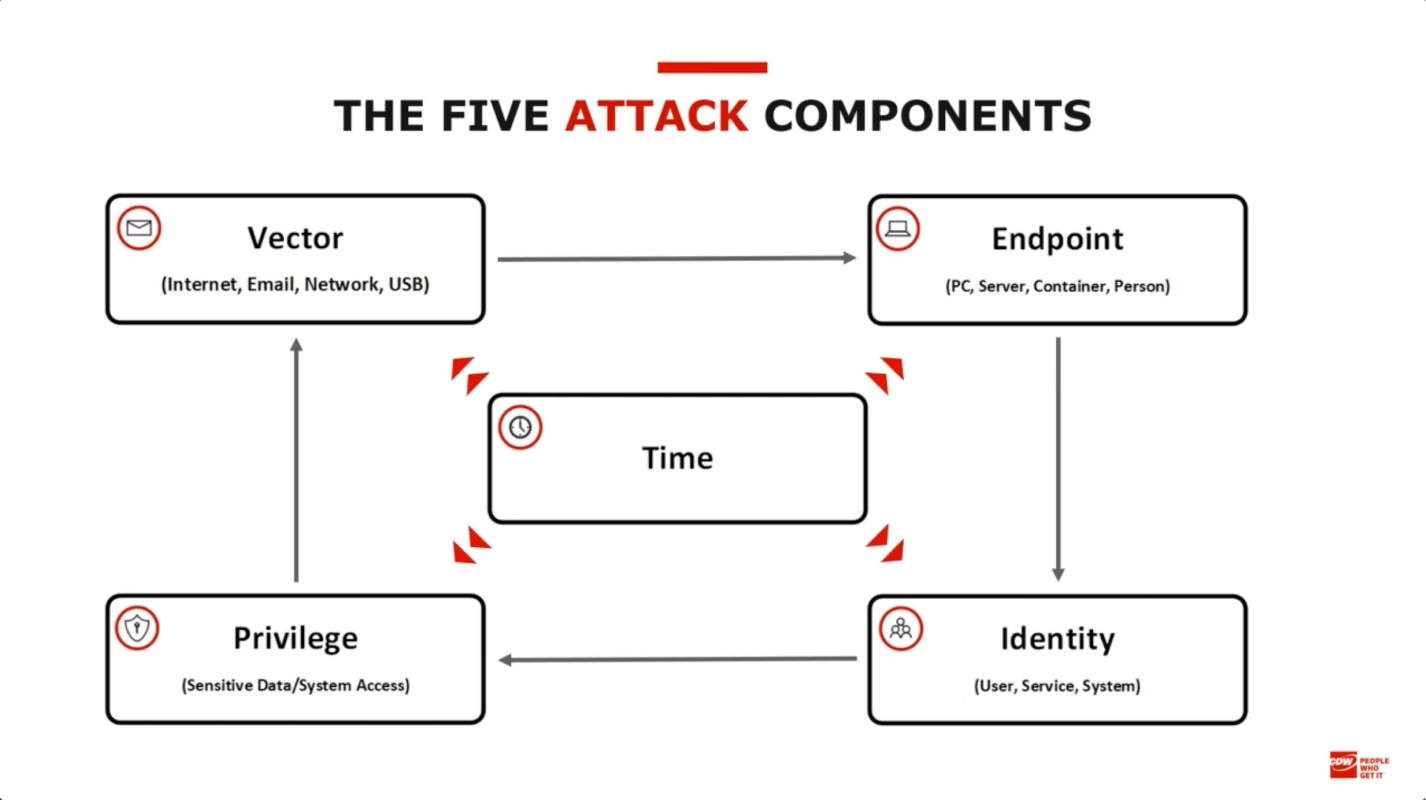
- Vectors: The open pathways that might help an attacker get in and out of the environment, such as internet, network, email, etc.
- Endpoints: The devices or individuals that may end up facilitating the execution of an attack, such as PCs, servers or users.
- Identities: The compromised credentials or accounts that the attacker assumes to make their way into the system.
- Privileges: The level of access or permission that the attacker gains, such as root, local admin or domain admin to spread the attack far and wide.
- Time: The longer the attacker stays in the environment, the more damage they can do.
All these components have a role to play in determining the severity of an attack. By ensuring each component is secured correctly, most attacks can be stopped dead in their tracks.
The attack story
Component
Role in an attack
Attack stage
Vectors
A phishing email containing a malicious link is sent to several mailboxes in a company
The attack has bypassed email monitoring but hasn’t affected anything yet
Endpoints
An employee inadvertently clicks on the link, downloading malware to their PC.
The employee’s PC has been infected with malware, allowing attackers to infiltrate other systems.
Identities
The malware travels through the company’s network, affecting other PCs, stealing usernames and passwords along the way.
All PCs connected to the originally infected PC have been affected. The identities have been compromised.
Privileges
The malware encounters an administrator’s PC that controls the security settings of the organization.
At this point, the attackers have found a way to bypass security controls as they have top-level privileges i.e., admin privileges.
Time
It has been 24 hours since the attack began.
If the attack is not detected quickly, the organization may end up losing all of their business data.
Build a stronger cybersecurity posture with Microsoft 365 Defender
What is Microsoft 365 Defender?
Microsoft 365 Defender is a cloud-based security solution designed to safeguard your organization’s digital environment. Built for Microsoft 365 environments and extended systems, it brings together various tools and features to protect against cyberthreats. It coordinates prevention, detection, investigation and response across Microsoft 365 services. Think of it as your security guardian, watching over your email, collaboration tools and more.
How does it protect Microsoft 365 users?
The tool leverages the power of the cloud and artificial intelligence to protect your organization from advanced threats. It integrates four Microsoft security services: Microsoft Defender for Endpoint, Microsoft Defender for Office 365, Microsoft Defender for Identity and Microsoft Cloud App Security.
By combining these services, Microsoft 365 Defender provides a comprehensive defence against sophisticated attacks across your endpoints, email, identities and cloud apps. It automatically detects, investigates and remediates threats, reducing the workload and complexity for your security teams.
It also provides rich threat intelligence and analytics to help you gain visibility and insights into your security posture and improve your security hygiene.
Step-by-step threat investigation with Microsoft 365 Defender
In order to investigate threats, Microsoft 365 Defender offers four modules that seamlessly work together to build attack stories. Each module looks at the attack from an investigative angle, such as where did the incident start, which device was affected and so on. This saves time zeroing in on the root cause of the attack and taking prompt action against an active attack.
Here are the four modules along with the investigation approach for each module.
Incidents
Incidents are collections of related alerts that indicate a potential compromise or attack on your organization. Incidents help you prioritize, investigate and respond to complex threats by providing a consolidated view of the affected entities, the timeline of events, the evidence and analysis and the recommended actions.
Investigation Approach
- View Incidents: Navigate to the Incidents dashboard to see a list of all incidents.
- Drill Down: Click on an incident to explore associated alerts, affected entities and the timeline.
- Analyze Evidence: Review evidence, such as process trees, network connections and file hashes.
- Take Action: Based on the analysis, take appropriate actions (quarantine, remediation, etc.).
Alerts
Alerts are notifications of suspicious or malicious activities detected by Microsoft 365 Defender across your devices, identities, email and cloud apps. Alerts provide details about the severity, category, status and source of the threat, as well as the affected entities and the suggested remediation steps.
Investigation Approach
- Alert Dashboard: Start by checking the flagged entries on this screen.
- Severity and Category: Prioritize based on severity and category such as low, medium or high.
- Affected Entities: Identify which users, devices or applications have been significantly affected.
- Contextual Data: Use the ‘explore additional context’ for details on timeline, related alerts, etc.
Hunting
Hunting is a proactive feature that allows you to search for indicators of compromise or anomalous behaviours across your Microsoft 365 environment. Hunting lets you use advanced query capabilities, custom detection rules and rich data sets to uncover and respond to hidden threats.
Investigation Approach
- Custom Queries: Create custom queries using KQL (Kusto Query Language).
- Data Exploration: Hunt across logs (e.g., Azure AD, Defender ATP, Exchange).
- Suspicious Patterns: Look for anomalies, unusual behaviour or known IOCs.
- Iterate and Refine: Continuously refine queries based on findings.
Threat Intelligence
Threat Intelligence is a feature that provides you with insights and context about the global threat landscape and the specific threats targeting your organization. Threat Intelligence helps you understand the tactics, techniques and procedures of threat actors. This includes the indicators of compromise, the reputation of domains and URLs with the impact of malicious files and emails.
- Indicators of Compromise (IOCs): Check if any IOCs match your environment.
- Tactics and Techniques: Learn about adversary tactics (e.g., lateral movement).
- Domain and URL Reputation: Assess the risk associated with domains and URLs.
- File and Email Prevalence: Understand common malicious files and emails.
Defend confidently with CDW’s cybersecurity expertise
Each organization approaches cybersecurity in a unique way, especially when it comes to Microsoft 365 apps, devices and services. CDW assesses your cybersecurity posture to empower your organization with always-on security delivered via managed Microsoft 365 Defender services.
Our powerful offering enables advanced threat detection, prevention investigation and remediation across your Microsoft environments. Our security analysts monitor, analyze and resolve incidents around the clock, leveraging Defender for Endpoint’s robust capabilities and reducing the time and cost of dealing with cyberattacks.
CDW’s service is based on the NIST Cybersecurity Framework, a risk-based approach that helps organizations achieve their ideal security posture. We also operate a national operations centre and a security operations centre, which act as a single point of contact and provide proactive notification, reporting and web portal access for customers.
Conclusion
As cyberattacks grow smarter, organizations need to modernize their cybersecurity practices for preventing data breaches. Microsoft 365 Defender is one such cloud-native solution that offers state-of-the-art investigation and remediation features for Microsoft 365 users, enabling them to centrally manage the entire fleet of devices and services.
CDW offers a simple yet risk-free approach to implement Microsoft 365 Defender, ensuring Microsoft services are always protected from threats.
